The rapid advancements in quantum computing which sparked growing concerns within the cryptocurrency sector late last year, particularly regarding Bitcoin’s long-term resilience seem to have once again resurfaced.
CryptoQuant, an on-chain data analytics platform, recently highlighted these risks in a series of posts on X titled “Quantum Computing is a Growing Risk for Bitcoin”.
The discussion focused on two critical aspects: Bitcoin mining security and private key vulnerabilities, both of which could face significant challenges as quantum technologies progress.
Quantum Threats to Bitcoin Mining and Network Security
Bitcoin’s proof-of-work (PoW) system relies on computational power to validate transactions and secure the network. The SHA-256 hash function, integral to Bitcoin mining, currently ensures strong security by, preventing malicious actors from tampering with the blockchain.
However, CryptoQuant warns that quantum algorithms, specifically leveraging advanced algorithms such as Grover’s, could substantially “accelerate hash-solving processes.”
If quantum computers become capable of outperforming classical mining hardware, it could tilt the balance of power in mining, enabling quantum-equipped miners to dominate block validation. This dominance would not only disrupt network consensus but also potentially compromise Bitcoin’s decentralized structure.
CryptoQuant emphasizes the importance of maintaining a significant share of non-quantum computing hash power in the network. A healthy and diverse mining ecosystem would mitigate the risks posed by any entity gaining disproportionate control via quantum technology.
While quantum supremacy in mining remains speculative at this stage, the ongoing developments in the field warrant close monitoring by stakeholders, including miners and developers.
Private Key Security: Vulnerabilities And Adaptations
Beyond mining, quantum computing also presents risks to BTC’s private key security. The Bitcoin network uses cryptographic systems to secure wallets and transactions, with public and private keys forming the basis of ownership.
According to CryptoQuant, Shor’s Algorithm could theoretically allow quantum computers to deduce private keys from public keys, thereby compromising wallet security.
Particularly vulnerable are Pay-to-Public-Key (P2PK) addresses, where the public key directly serves as the wallet address. In contrast, Pay-to-Public-Key-Hash (P2PKH) addresses provide an additional layer of security by hashing public keys.
Private Key Security & Quantum Risks
Another major concern is Shor’s Algorithm, which could, in theory, allow quantum computers to find private keys from public keys. ‘Pay to public key’ (P2PK) addresses are most vulnerable to quantum attacks, as the public key serves directly… pic.twitter.com/q2NBvbwGLe
— CryptoQuant.com (@cryptoquant_com) January 7, 2025
However, when BTC from these addresses is transferred, the public key is exposed, increasing susceptibility to quantum attacks. CryptoQuant also observed a notable increase in P2PKH address usage, rising by 14% in recent months.
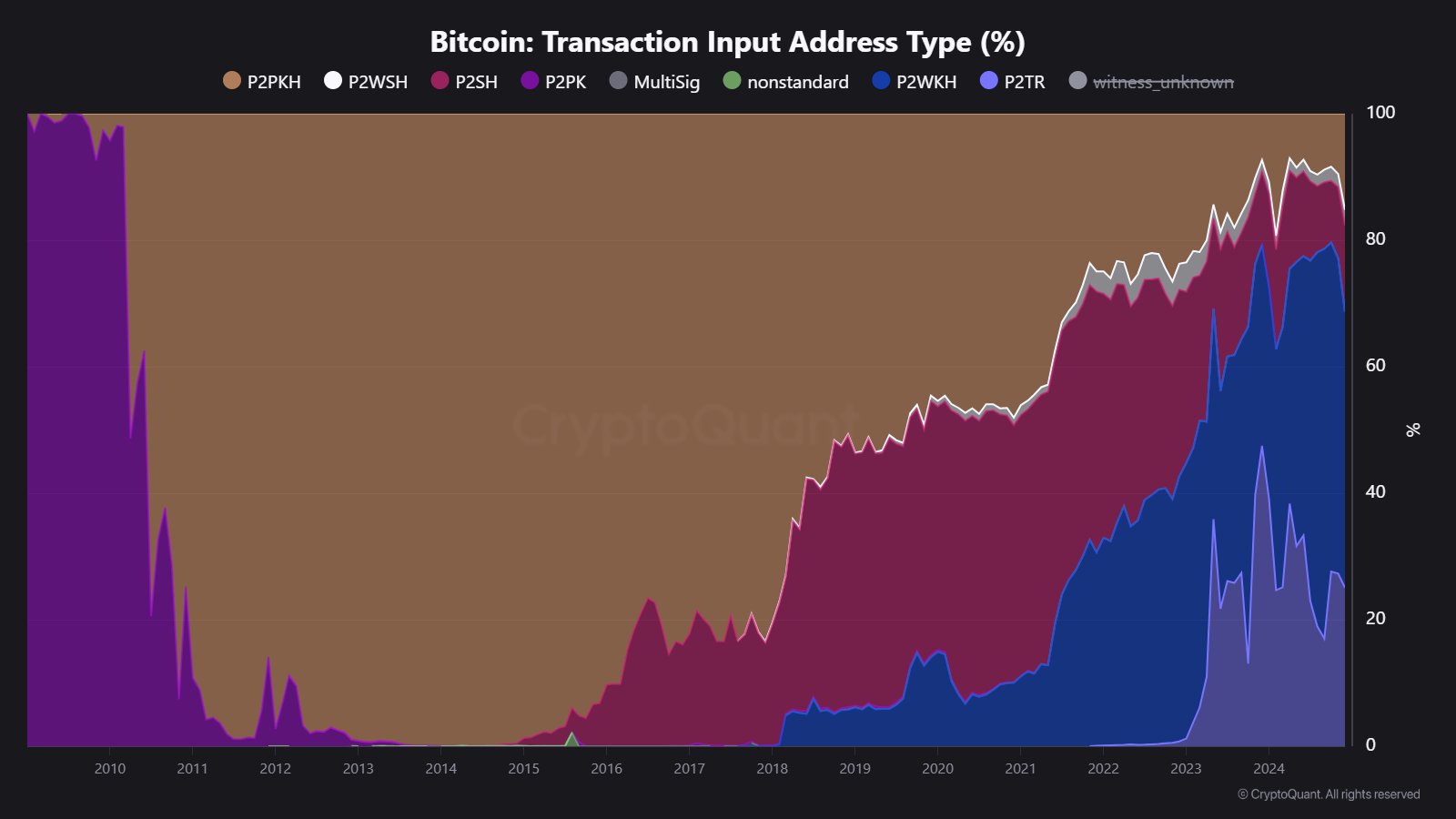
While the exact cause of this shift remains unclear, it suggests heightened awareness and caution among Bitcoin holders regarding quantum vulnerabilities.
Featured image created with DALL-E, Chart from TradingView

You can get bonuses upto $100 FREE BONUS when you:
💰 Install these recommended apps:
💲 SocialGood - 100% Crypto Back on Everyday Shopping
💲 xPortal - The DeFi For The Next Billion
💲 CryptoTab Browser - Lightweight, fast, and ready to mine!
💰 Register on these recommended exchanges:
🟡 Binance🟡 Bitfinex🟡 Bitmart🟡 Bittrex🟡 Bitget
🟡 CoinEx🟡 Crypto.com🟡 Gate.io🟡 Huobi🟡 Kucoin.














Comments