
A digital signature is a cryptographic method used to ensure the validity and integrity of digital data. We can think of it as a digital equivalent of a traditional handwritten signature, but with more complexity and security.
Simply put, a digital signature is a code linked to a message or document. Once formed, the code verifies that the communication was not tampered with on its journey from sender to receiver.
Although the notion of utilizing cryptography to secure communications stretches back to ancient times, digital signature systems became possible in the 1970s, owing to the advent of Public-Key Cryptography (PKC).
To understand what a digital signature is in bitcoin and how it works, we must first grasp the fundamentals of hash function and public-key cryptography.
Key Takeaways
- Digital signatures in Bitcoin are used to prove the authenticity of transactions and the ownership of the funds being transferred.
- Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate a unique signature for each transaction.
- The signature is included in the transaction data and verified by other nodes in the network before the transaction can be added to the blockchain.
- Digital signatures help to ensure that a transaction has not been tampered with and was initiated by the owner of the private key associated with the public address used in the transaction.
- Digital signatures in Bitcoin are an essential aspect of public key cryptography, a fundamental technology underlying the security of the Bitcoin network.
What Is a Digital Signature?
A digital signature is a mathematical technique used to validate the authenticity and integrity of a message or a digital document. It's an asymmetric encryption technique that uses a private key to encrypt a hash of the document and a matching public key to decrypt it.&
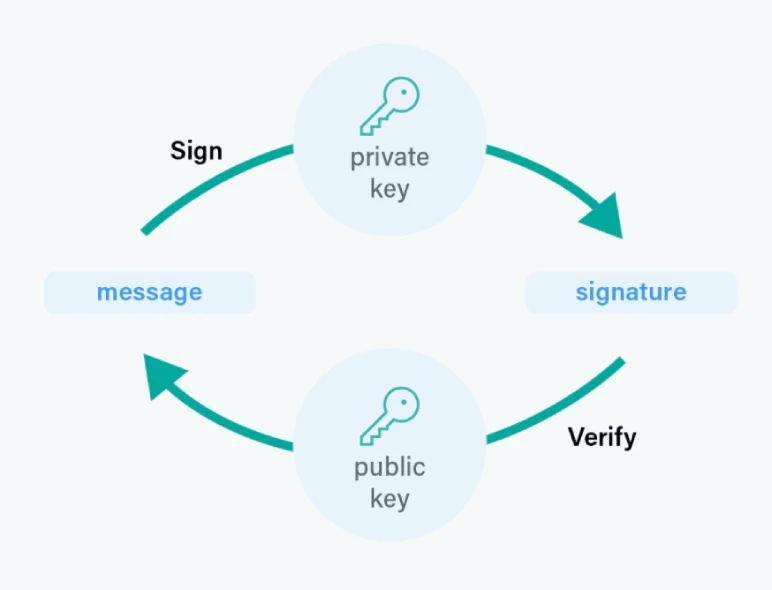
This enables the document's recipient to confirm that the information in digital messages has not been tampered with and was sent by the stated sender. By encrypting the entire message with the recipient's public key, we can ensure that only the recipient, who is in possession of the corresponding private key, can read the message. We can also verify the user's identity using the public key and check it against a certificate authority.
Digital signatures are extensively employed in electronic communications and online banking to assure the validity and integrity of the information being transmitted.
Hash Function
Hashing is a key component of the digital signature system. The Cybersecurity and Infrastructure Security Agency (CISA) defines a hash function as:
A fixed-length string of numbers and letters generated from a mathematical algorithm and an arbitrarily sized file such as an email, document, picture, or other type of data. This generated string is unique to the file being hashed and is a one-way function—a computed hash cannot be reversed to find other files that may generate the same hash value.
A hash function can be used to convert an arbitrary input into the proper format. When paired with cryptography, cryptographic hash functions can provide a hash value (digest) that serves as a unique digital fingerprint. This means that every modification in the input data (message) results in an entirely new outcome (hash value). As a result, cryptographic hash functions are commonly utilized to validate digital data.
Public-Key Cryptography (PKC)
Public-key cryptography (PKC) is a cryptographic technique that employs a public key and a private key. The two keys have a mathematical relationship and can be utilized for data encryption as well as e-signatures.
PKC is a more secure encryption technology than symmetric encryption algorithms. Unlike prior systems, which used the same key to encrypt and decrypt data, PKC allows for data encryption with the public key and data decryption with the associated private key.
Additionally, the PKC method can be used to generate an e-signature. In essence, the process involves hashing a message (or electronic data) along with the signer's private key. The recipient of the message can then use the signer's public key to validate the signature.
Digital signatures may require encryption in some circumstances, although this is not always the case. For example, the Bitcoin blockchain employs PKC and digital signatures; however, contrary to popular belief, no encryption is involved. Bitcoin uses the so-called Elliptic Curve Digital Signature Algorithm (ECDSA) to authenticate transactions.
Fast Fact
1. The first digital signature algorithm called the "Diffie-Hellman Key Exchange," was proposed by Whitfield Diffie and Martin Hellman in 1976.
2. RSA, invented in 1977 by Ron Rivest, Adi Shamir, and Leonard Adleman, is the most commonly used digital signature algorithm.
How Do Digital Signatures Work?
Digital signatures use a combination of public key cryptography and hashing. The process typically involves the following steps:
- The entity sending the electronic document uses a private key to create a hash of the document, i.e., a fixed-length string of characters representing the document's contents.
- The sender then uses their private key to encrypt the hash, creating the digital signature.
- The digital signature and the digitally signed document are sent to the recipient.
- The recipient uses the sender's public key to decrypt the digital signature, and this gives them the original hash of the document.
- The recipient then uses the same hash algorithm to create a new hash of the received document.
- The recipient then compares the newly created hash with the decrypted hash from the signature; if both are the same, it implies that the document has not been tampered with.
- The sender’s public key is also used to verify that the signature was created by the claimed sender and not an imposter.
In this way, digital signatures ensure the authentication and integrity of a digital document, verifying that it has not been tampered with and was transmitted by the stated sender. Hence, a digital signature refers to a more secure electronic signature generated using a digital certificate and cryptographically bound to the document using public key infrastructure (PKI).
Digital Signature in Blockchain
Digital signatures play a crucial role in establishing trust in the blockchain. In a blockchain network, transactions are grouped into blocks and added to a chain of blocks in a linear, chronological order. Each block contains a list of transactions, along with a digital signature, called a "hash," that links it to the previous block in the chain.
This signature, called a "nonce" is a number generated by the miner creating the block and is added to the block header, which is then hashed. The miner is trying to find a nonce that will result in a specific pattern of leading zeroes in the block hash.
All parties using digital signature technology must have faith that the person who created the signature maintains the private key secret. If malicious actors gain access to the private key, they can forge digital signatures in the private key holder's name. Using digital signatures along with PKI or PGP reduces the possible security issues connected to transmitting public keys by validating that the key belongs to the sender and verifying the sender's identity. The security of a digital signature depends on protecting the private key. Moreover, without PGP or PKI, proving someone's identity or revoking a compromised key is impossible.
Pro-Tip: Certificate Authorities (CAs), a type of Trust Service Provider, are widely accepted as reliable organizations for ensuring key security and providing the required digital certificates. The certificate is used to confirm that the public key belongs to the specific organization. Both the entity sending the document and the recipient signing it must agree to use a given CA.
Digital Signatures in Bitcoin
A digital signature in Bitcoin is a mathematical algorithm that uses cryptography to verify the authenticity of a transaction. It allows a Bitcoin user to prove they are the owner of a particular public address with authority to transfer the funds associated with that address. Digital signatures in Bitcoin use the Elliptic Curve Digital Signature Algorithm (ECDSA) to generate a unique signature for each transaction. This signature is included in the transaction data and is verified by other nodes in the network before the transaction can be added to the blockchain.
For example, if 'X' wishes to transfer 'Y' 1 bitcoin, X must sign a transaction using its private key and submit it to network nodes. Miners having the 'X' public key will then examine the transaction conditions and validate the signature. When the legitimacy of a transaction is confirmed, the block containing that transaction is available for finalization by a validator/miner.
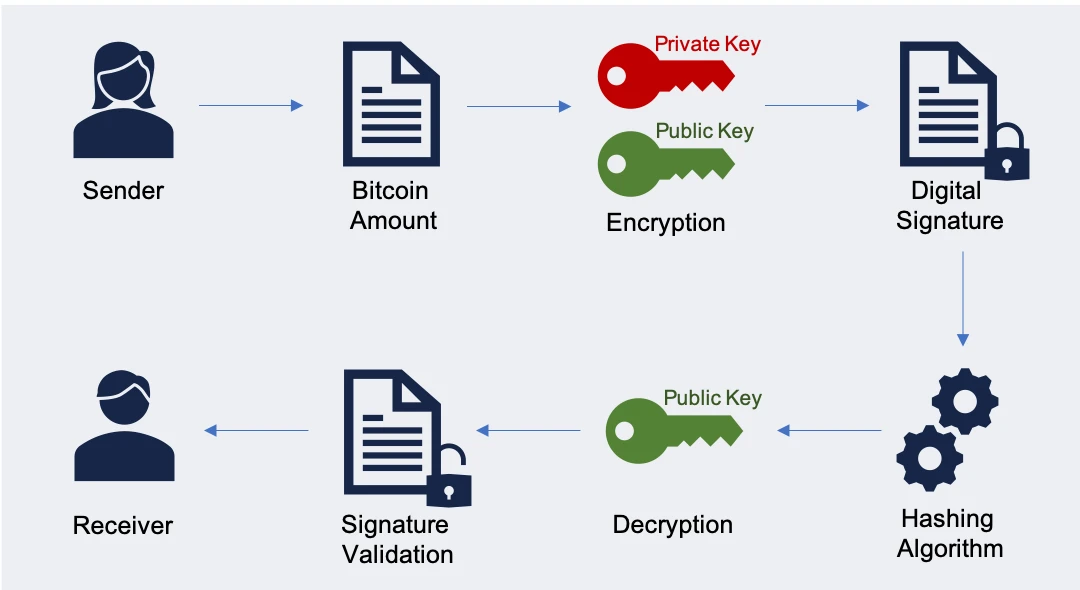
What Is a Bitcoin Transaction?
A Bitcoin transaction is a transfer of bitcoin from one address to another that is recorded on the Bitcoin blockchain. It consists of one or more inputs and one or more outputs and includes a digital signature to authorize the transfer. The inputs specify the addresses and amounts of bitcoin being transferred, while the outputs specify the addresses and amounts of bitcoin being received. Once a transaction is included in a block that's added to the blockchain, the transaction is confirmed, and the transferred bitcoins are considered spendable.
How Do Bitcoin Transactions Work?
Let’s take the example of Alice and Bob to learn what happens inside transactions and about cryptography usage in Bitcoin.
The diagrams below depict Alice sending satoshis to Bob and Bob spending them. Alice and Bob will utilize the most popular Pay-to-Public-Key-Hash (P2PKH) transaction type. P2PKH allows Alice to send satoshis to a standard Bitcoin address and Bob to spend those satoshis using a simple cryptographic key pair.
Later, Bob chooses to spend Alice's UTXO:
Bitcoin Mining and Proof-Of-Work Consensus Mechanism
Bitcoins are generated via mining. To generate a block on the blockchain, a miner must solve a complex cryptographic problem, and the answer is a sequence of integers included within the block known as the nonce. This method of determining the nonce is known as Bitcoin mining and involves many miners worldwide.
Bitcoin mempool collects an unconfirmed transaction until it's processed and added to the block. There are several fixed criteria for the block, such as the previous block hash, the characteristics of transactions in the current block, etc. The nonce is the sole parameter that can be modified. The miner's duty is to identify the nonce that will allow the candidate block to meet the difficulty target. The only method to get the nonce is to attempt several nonce values, compute the hash of the new block (last block hash id | block with transactions | nonce, where '|' indicates concatenate), and see if the hash meets the difficulty threshold (get a string that has a certain number of zeros).
The miner's responsibilities are as follows:
Bitcoin's Proof-of-Work consensus employs two successive SHA-256 hashes, where the first 32 of 256 hash bits must initially be zero. However, the Bitcoin network changes the difficulty level regularly to maintain the average pace of block generation at 10 minutes.
Electronic Signatures vs. Digital Signatures
Digital signatures are a type of electronic signature used to sign documents and messages. A digital signature can be expressed digitally in electronic form and associated with the representation of a record. While all digital signatures are electronic signatures, the contrary is not necessarily true.
The key distinction between them is the authentication technique. Such cryptographic technologies as hash functions, public-key cryptography, and encryption methods are used in digital signatures.
E-signatures are also defined in the Electronic Signatures Directive, which the European Union (EU) passed in 1999 and repealed in 2016. It regarded them as equivalent to physical signatures. This act was replaced with eIDAS (electronic identification authentication and trust services), which regulates e-signatures and transactions. eIDAS defines the 3 levels of electronic signatures: an electronic signature (sometimes referred to as a “simple” signature), an advanced electronic signature (AdES), and a qualified electronic signature (QES). AES adds identity verification, requiring signatures to be uniquely linked to the signatory and capable of identifying the signer. The signature record can show evidence of tampering. QES requires face-to-face identity verification or the equivalent.
The United States passed the Electronic Signatures in Global and National Commerce Act (ESIGN) in 2000.
Many governments and corporations also use smart cards to ID their citizens and employees.
What Are the Benefits of Digital Signatures?
Now that we have a general idea of a digital signature, let's learn about its advantages! The main advantage of digital signatures is their security. Digital signatures comply with regulations in many countries and provide the highest level of identity assurance when dealing with digital documents.
Digital signatures employ the following security characteristics and methods:
- Personal identification numbers (PINs), passwords, and codes. They are used to identify and verify a signer's identity and validate their signature. The most common use cases are email, username, and password.
- Cyclic Redundancy Check (CRC). An error-detecting code and verification function used to detect changes to raw data in digital networks and storage devices.
- Asymmetric Cryptography. A public key algorithm comprising a private key and public key encryption and authentication.
- Certificate Authority (CA) Validation. CAs issue digital signatures and serve as a trusted third party by accepting, verifying, issuing, and maintaining digital certificates. The use of CAs aid in the prevention of the fabrication of a forged digital certificate.
- Trust Service Provider (TSP) Validation. A TSP is a person or legal entity that validates digital signatures on behalf of businesses and provides signature validation reports.
- Traceability. Digital signatures create an audit trail to simplify internal record-keeping for enterprises. There are fewer possibilities for a manual signee or record keeper to make a mistake or misplace anything when everything is recorded and saved digitally.
Final Thoughts
Digital signatures can provide evidence of the origin, identity, and status of electronic documents, transactions, or digital messages. Signers can also use them to acknowledge informed consent. The U.S. Government Publishing Office (GPO) publishes electronic versions of budgets, public and private laws, and congressional bills with digital signatures.
Digital signatures are used in the blockchain to sign and approve Bitcoin transactions to ensure that coins are spent by persons with the associated private keys.
Although we've been utilizing electronic and digital signatures for years, there is still much space for improvement. While a large chunk of today's bureaucracy still uses paper documents, we'll undoubtedly see greater acceptance of digital signature techniques as we transition to a more digitalized system.
You’re welcome to visit our CoinStats blog to get a broader perspective on decentralized finance and how it seeks to empower people. You can also read our articles, such as What Is DeFi, explore our in-depth buying and staking guides on various cryptocurrencies, such as How to Buy Bitcoin, How to Stake MATIC, How to Stake Ethereum, How to Buy Cryptocurrency and learn more about wallets and exchanges, portfolio trackers, etc.

You can get bonuses upto $100 FREE BONUS when you:
💰 Install these recommended apps:
💲 SocialGood - 100% Crypto Back on Everyday Shopping
💲 xPortal - The DeFi For The Next Billion
💲 CryptoTab Browser - Lightweight, fast, and ready to mine!
💰 Register on these recommended exchanges:
🟡 Binance🟡 Bitfinex🟡 Bitmart🟡 Bittrex🟡 Bitget
🟡 CoinEx🟡 Crypto.com🟡 Gate.io🟡 Huobi🟡 Kucoin.












Comments